Risk Management
- Related ESG :
- E S G

Management approach
Policy and approach
As well as establishing a “Risk Management Basic Policy” that outlines our fundamental stance on risk management activities,Toyobo group is identifying various types of risk that could pose a threat across the entire range of our business activities, and are managing risk appropriately according to the characteristics of each risk. In an emergency, we immediately set up a task force under the instruction of the relevant corporate officer, and bring the crisis under control through a swift response. By putting these systems in place and conducting the initiatives, we work hard to earn the trust of our customers, the local community, and our shareholders and other stakeholders.
< Basic policy on business risk >
1. Toyobo group has a system for identifying the location of risks and the size of their impact (visualization)
2. Allocate resources appropriately to avoid or reduce identified risks
3. We will deepen and upgrade our activities by continuing to run PDCA
4. Enhance sensitivity and responsiveness to risks by each individual through information sharing, training, etc (eliminate ignorance)
5. All employees participate in risk management activities by personalizing them
Business risks
The main risks recognized that could have a material impact on Toyobo group's operating results and financial position are as listed below. The list does not include all the risks related to Toyobo group.
Forward-looking statements were determined by the group as of fiscal 2024-end.
< Incurred or highly probable risks >
- (1)
- Occurrence of disasters, accidents, and infections
- (2)
- Further worsening of political and economic situations
- (3)
- Inappropriate behavior or similar in details of third-party certification registration
< Medium- to long-term risks >
- (4)
- Purchase of raw materials
- (5)
- Product defects
- (6)
- Securing of human resources
- (7)
- Climate change
- (8)
- Environmental burden
- (9)
- Information security
- (10)
- Laws, regulations and compliance
- (11)
- Overseas business activities
- (12)
- Litigation
< Financial risks >
- (13)
- Large forex movement
- (14)
- Large rise in interest rates
- (15)
- Sharp drop in share prices
- (16)
- Impairment loss of fixed assets
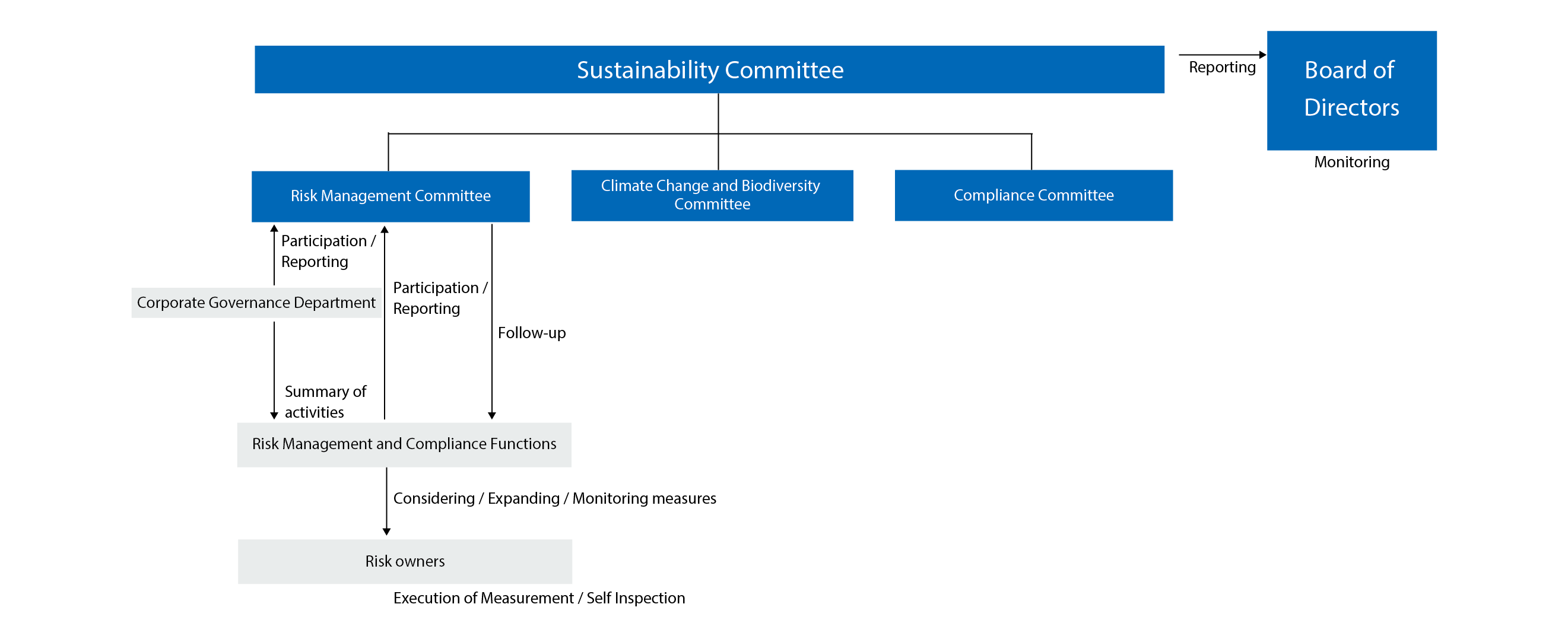
Structure
On April 1, 2021, Toyobo group established a Risk Management Committee headed by the President for centralized management of risks throughout the group. The committee comprises members of the Board of Management and Controlling Supervisors as well as members nominated by the chair, and in fiscal 2024, it convened twice.
This Risk Management Committee brings together risk management activities (identification, analysis, evaluation, and response), as well as formulating risk management policies for the group as a whole. It is working to strengthen our risk management structure by aiming to build effective and sustainable organizations and approaches.
Management structures and processes
Initiatives
As part of our management policy, we seek to be a company that is able to grow sustainably by shifting from the survival-based thinking of the past to a sustainable growth orientation. We establish self-directed management activities appropriate to business areas and roles, assess company-wide risks and work toward their prevention and early detection, and, united as a group, will build a system to advance measures for preventing recurrence of risks.
As a starting point for these activities, we conducted an assessment of company-wide risks. We identified serious risks from the results of evaluations in terms of the two axes of severity of impact and likelihood of occurrence, and monitor these risks regularly.
Major risks defined by the group include those related to quality, safety and security disaster prevention, and legal compliance. In the Major Risks Survey of the group companies, which was continuously conducted from FY2023 to the end of the first half of FY2025, we ascertained the status of risk responses at each company through dialogue based on possible risk scenarios. As a result of the risk assessment including overseas bases, we confirmed that there were no risks, including legal compliance risks, that would make it difficult for the group to continue its business.
For risk items that require measures based on common frameworks, such as cybersecurity response and virus infection prevention, we collaborated with departments managing risk management to implement uniform risk measures, regardless of domestic or overseas locations. However, for risk items requiring regulatory compliance measures, we have recognized that each group company is taking independent risk measures in their operating regions.
Any detected items that are common across the group and that require attention are reported to the Risk Management Committee. Group-wide risk reduction activities are undertaken in collaboration with the departments managing risk management, business divisions, and group companies.
Data security, privacy
- Related ESG :
- S G

Policy and approach
Today, as significance of information increasingly grows, how a company utilizes necessary information, advances development of products and technologies, and develops businesses in line with the times is a crucial factor in the company's survival.
The improper management of information can also have severe repercussions to a company from legal and social standpoints. As stated in our TOYOBO Group Charter of Corporate Behavior, our group must properly manage information and prevent problems involving information security from occurring if we are to contribute to society and remain a company that earns people's trust.
Restated, it is necessary that every one of our officers and employees recognizes the importance of information security and the information assets that are the key to corporate survival, and, while effectively utilizing our information assets throughout the organization, maintains and secures the confidentiality, integrity, and availability of those information assets. Based on this thinking, our group has declared our basic policies as follows:
< Information security policy (theme excerpts only) >
- 1. Management system
We will establish an information security management system with responsible executives placed at top, and will strive for proper management in line with the importance of and risks to information. - 2. Legal compliance and internal regulations
We will establish internal rules in accordance with information security-related laws and ordinances, countries' national guidelines, and other social norms, and will take strict action against violators of these rules. - 3. Education and training
We will conduct education and training for our employees on an ongoing basis to ensure that information assets are used properly, and will work to enforce compliance with rules. - 4. Operation of information systems
We will enact appropriate measures and endeavor to operate information systems stably to prevent unauthorized intrusion and the leak, falsification, loss, theft, destruction, obstruction of use, etc. of information assets. - 5. Handling of incidents
In the event of a problem involving information security, we will enact measures to minimize the damage, promptly investigate the cause, and strive to prevent recurrence.
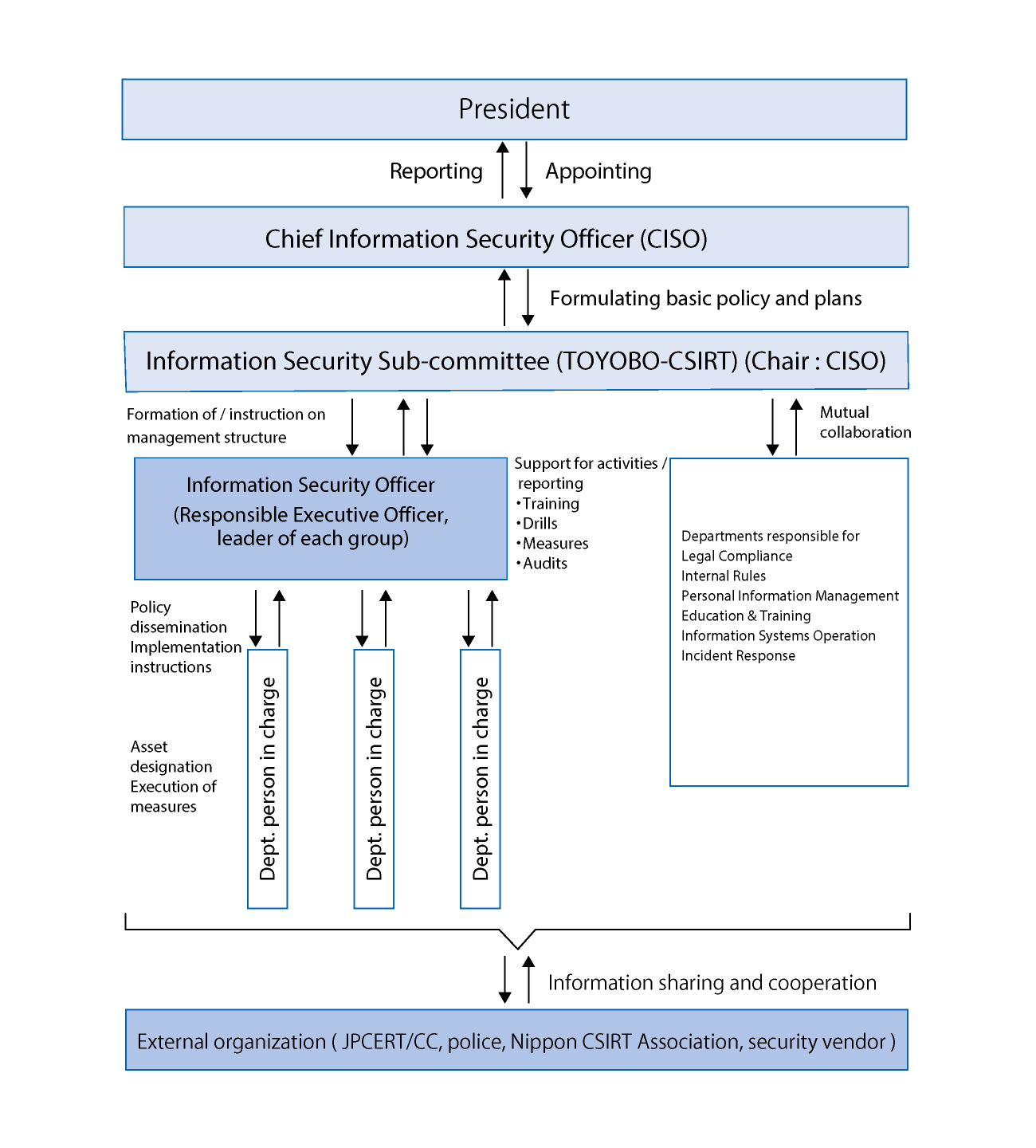
Structure
Our group has established the TOYOBO-CSIRT, led by a CISO appointed by top management, as an organization to promote information security measures and activities. TOYOBO-CSIRT assesses the status of information security across the company, formulates basic policies, maintains management systems, and implements and supervises specific measures.
To advance measures based on the decisions of TOYOBO-CSIRT, we have established a front-line operations team. We also convene TOYOBO-CSIRT on a regular basis to evaluate risk countermeasures, each time also reporting on activities related to information security.
By expanding the activities of TOYOBO-CSIRT throughout our entire group, we will work to instill understanding of information security and enforce the protection of information assets, creating a state across the group in which data, security, and privacy are secured and trusted.
Our IT and DX Planning Department, which has acquired ISO 27001* certification, undergoes a yearly external audit based on ISO 27001 to confirm proper operation of information security management. The Department conducts on-duty management at five business sites of the company (the head office, Research Center, Tsuruga Research and Production Center, Iwakuni Production Center, Inuyama Plant: 50% of all business sites), and also performs comprehensive management of other business sites through the Department's management system.
- An international standard for information security management systems
Toyobo group information security management structure
We assign a person responsible for information security to each department and built a company-wide information management system to ensure the required information security level.
Targets and KPIs
< Targets >
Toyobo group establishes a structure to ensure cyber security as well as deepening employee understanding of information security and thoroughly ensuring protection of information.
< KPIs and results >
| Initiatives | KPIs | Targets (FY2024) | Results (FY2024) |
|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
- The scope covers TOYOBO CO., LTD., its subsidiaries, as well as affiliates accounted for by the equity method and over which Toyobo has significant influence.
- *Specific measures aimed at consolidated subsidiaries
・Application of Information Security Policy
・Roll out of measures to strengthen IT/OT
Initiatives
Protection of personal information
Awareness of the protection of personal information is increasing worldwide. Toyobo group is revising our internal regulations to ensure handling of personal information in compliance with Japan's Act on the Protection of Personal Information and China's Personal Information Protection Law.
We will continue to strengthen our systems for protection of the personal information of customers, our business associates, shareholders, and employees.
Promotion of digitalization
Digitalization is advancing rapidly with the development of IT. Amid this change, Toyobo group is advancing the construction of an IT system infrastructure that encompasses the entire value chain and is tackling the transformation of our business style and the creation of new solutions, making full use of digital technologies. By doing so, we seek to not only improve the efficiency of work but also strengthen our provision of value to society and to customers.
We have promoted the digitalization of business by actively incorporating IT in our operations, including streamlining sales activities through IT tools, using IT to enhance manufacturing control, and enhancing the efficiency of intellectual property management through AI.
In April 2020, we established a Digital Strategy Department as a dedicated department to advance such activities on a company-wide basis. In April 2023, we integrated systems subsidiary Toyobo Information System Create Co., Ltd. with this department to create the IT and DX Planning Department. This established a system that is capable of quickly responding to changes in the business environment, wielding digital technology as a competitive advantage.
In fiscal 2024, our initiatives were evaluated to meet the certification criteria set by the Ministry of Economy, Trade and Industry (METI), and we were recognized as a DX Certified Business Operator*.
In accordance with our reorganized road map to achieve our vision for 2030, we will strengthen the group’s internal IT system infrastructure and advance digital transformation.
The IT and DX Planning Department has become a “bridge” connecting digital and business, and has begun initiatives to implement organizational and business transformation across the entire company and across its businesses. All of our group companies will cooperate to increase the scope and degree of utilization of digitalization.
- This system is certified by the government under the Digital Governance Code compiled by METI. It recognizes companies that promote initiatives such as formulating visions and establishing systems for achieving DX, based on the Act on Facilitation of Information Processing.
Education and awareness-raising activities
As a part of our education and awareness-raising activities, we deliver the “Cyber Security Communication” newsletter every month to all employees of Toyobo group in Japan and overseas. We also conduct testing of security comprehension twice a year to let employees self-check and reflect on their understanding of our education and awareness-raising activities.
In conjunction with Compliance Enhancement Month in fiscal 2024, we conducted training for managers and disseminated information at all workplaces on the theme of information security, and conducted video-based education for all employees. In addition, we conducted information security education for all employees of overseas group companies in an effort to enhance awareness across the group.
Information security measures
Cyber attacks are intensifying year by year, often targeting overseas sites and group companies. In response, we are working to raise the information security measures of our domestic and overseas affiliates to the same level as that of our headquarters, and to strengthen information security across the group. Specific measures include communication of policies and regulations and support for their improvement, support for the introduction of education for employees and managers, implementation of targeted email attack drills, deployment and inspection of IT reinforcement measures, and continuous strengthening of our contact system for security and incident response.
We conduct biannual targeted email attack drills, varying the level of difficulty and subject matter each time, for all employees of Toyobo group in Japan and overseas. To ensure the safety of customer information and our internal information, including confidential information, we continually assess new threats and take appropriate countermeasures, including strengthened monitoring of both IT and OT*, patching of vulnerabilities, and prevention of unauthorized intrusions.
- IT (Information Technology), OT (Operational Technology)
Protection of information in outsourcing
When outsourcing information assets containing confidential information, the company has established outsourcing management rules for the following procedures: (1) evaluation and contracting of outsourcing partners; (2) monitoring of operations after the contract has been concluded; and (3) handling of information assets after the contract has been terminated.
When newly implementing operations to be outsourced (hereinafter referred to as "specified operations"), the department outsourcing the specified operations evaluates whether or not the candidate companies conform to the "outsourcer evaluation criteria" in accordance with these rules. After the selection, the department submits the 'outsourcer evaluation results' to the head of the information security department for approval. In addition, it is also stipulated that the implementation status of specified operations is to be regularly evaluated by the head of the information security department.
The “outsourcer evaluation criteria” are clearly stated in the “Information Security Policy”.
Initiative participation
Under the idea that we must address cyber attacks not only in our group companies and supply chains but across society as a whole, we engage in active information sharing in cooperation with the JPCERT Coordination Center and the Nippon CSIRT Association.
Business continuity management (BCM)
Policy and approach
Our group aims to establish Business Continuity Management (BCM) to prepare for various risks such as natural disasters, accidents, and pandemics, which could disrupt business continuity. We prioritize the preservation of human life, aim to promptly restore operations, and fulfill our supply responsibilities. In fiscal 2025, as part of the Sustainability Committee’s activities, the President will oversee the establishment of BCM and work to enhance the Business Continuity Plan (BCP).






